- USDT(TRC-20)
- $66,870.0
Are you tired of not being in control of someone else's iPhone? Your husband? Your Children? Your Sugar baby?
Well, now you can take over their iPhone from far away with our professional service!
Just by sending a simple text message, you can have access to all their messages, photos, and even make changes to their phone without them knowing.
And the best part? It's all done through a beginner friendly convenient web panel that we will help set up for you.
Don't miss out on this amazing opportunity to finally infiltrate your target iPhone.
Features:
Pricing:
Note: After using autoshop(link above), you will receive automatically the link where you can input the numbers in the web dashboard and sms will be sent by our system to target to infect their system without them clicking on any link. In case of any issue with the use of our service, you can contact our support Telegram anytime:

For Professional Hackers:
Exploit Source Code + Guide to do each attack by yourself: $ 30,000 (only selling 3 copies)
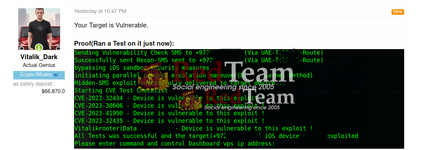
CVE Chain Exploited by my private toolset:
CVE-2023-32434 - C#
CVE-2023-38606 - C++
CVE-2023-41990 - C++
CVE-2023-32435 - C++
and 3 more secret zero days.
Sold: 2/3 as of 21.06.24
Contact:
 I accept @Blyckat Escrow
I accept @Blyckat Escrow
How to buy Crypto Anonymously?
Well, now you can take over their iPhone from far away with our professional service!
Just by sending a simple text message, you can have access to all their messages, photos, and even make changes to their phone without them knowing.
And the best part? It's all done through a beginner friendly convenient web panel that we will help set up for you.
Don't miss out on this amazing opportunity to finally infiltrate your target iPhone.
Features:
- Remote access and control of the target iOS device
- Keylogging capabilities
- Remote file transfer and management
- Ability to view and manipulate the device's camera and microphone
- Real-time screen viewing and recording
- Stealth mode to avoid detection by the target user
- Encryption for secure communication
- Multi-platform support for accessing the device from different operating systems
- Multi-lingual user interface for global usability
- Customizable settings and configurations for specific needs and preferences
Pricing:
- FREE - Target Vulnerability Test (What does it mean?)
- $ 3000 - 1 single target hack (Just deposit to leet escrow and provide the target phone number, we will infect the victim iphone and send you link to web RAT panel to track them - we give a 3 month warranty to stay in target system) .
- 10% OFF ($2700 for 3 targets) if you buy through My autoshop (BTC, LTC, XMR Accepted):

For Professional Hackers:
Exploit Source Code + Guide to do each attack by yourself: $ 30,000 (only selling 3 copies)
CVE Chain Exploited by my private toolset:
CVE-2023-32434 - C#
CVE-2023-38606 - C++
CVE-2023-41990 - C++
CVE-2023-32435 - C++
and 3 more secret zero days.
Sold: 2/3 as of 21.06.24
Contact:

How to buy Crypto Anonymously?
This offer contains a Telegram chat link for which The Off-Shore Club (Ex Underground Forums) is not responsible. If you want safety, use RTM escrow.